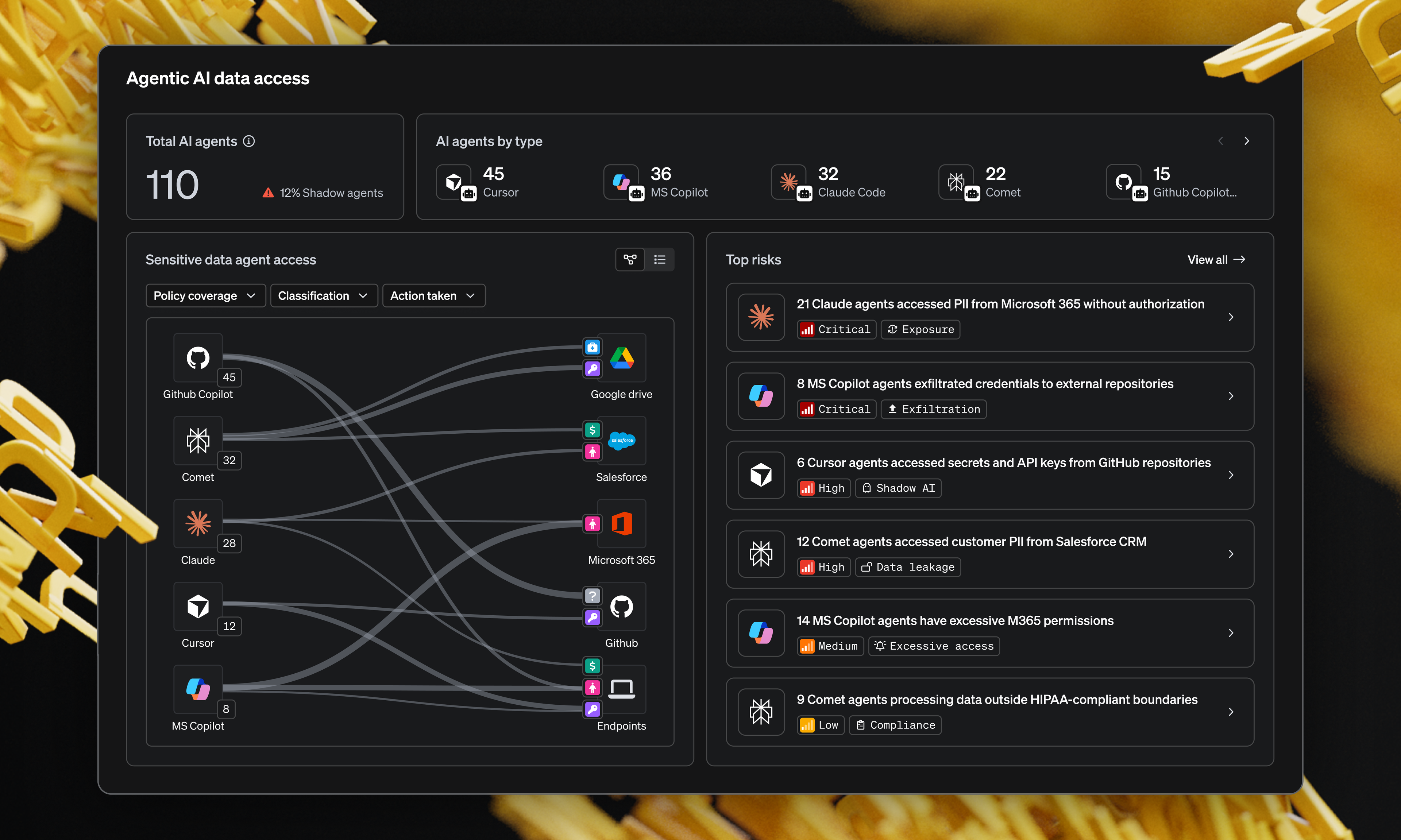
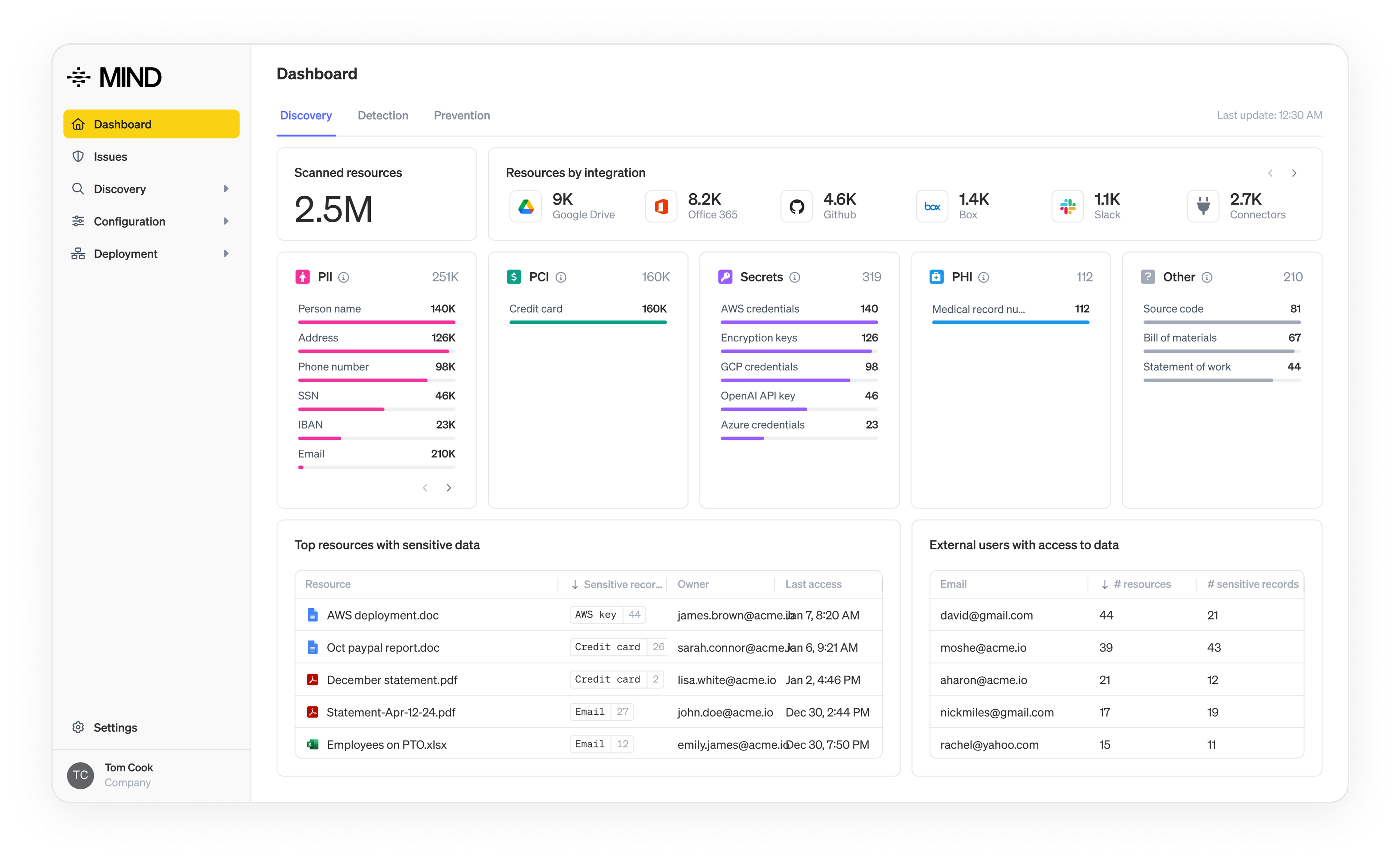
Data loss prevention (DLP) has been around for decades, but the way organizations use data has changed dramatically. Files no longer live in a single data center. They move across cloud apps, personal devices, collaboration tools and AI systems. As a result, DLP solutions have evolved into three primary categories: network DLP, endpoint DLP and cloud-based DLP.
Each type addresses a different part of the data lifecycle. Understanding how they work and where they fit helps teams make more informed decisions about protecting sensitive information.
What are the main types of DLP Solutions?
Network DLP
Network DLP is one of the earliest forms of data loss prevention. It focuses on monitoring and controlling data as it moves across the network perimeter. These solutions typically inspect traffic leaving the organization through email gateways, web proxies or network appliances.
The core strength of network DLP is visibility into outbound traffic. It can detect sensitive data being sent via email, uploaded to external websites or transferred through network protocols. When a policy violation occurs, the system may block the transmission, quarantine the content or alert security teams.
However, network DLP relies heavily on traffic inspection and predefined rules. It often struggles with encrypted traffic, which now represents a large portion of network activity. It also has limited insight into user intent or business context. A file transfer that looks risky on the network may actually be a legitimate business process.
Network DLP is most effective in environments where data flows through controlled gateways and where encryption and cloud usage are limited. In modern environments, it often serves as one layer of protection rather than a complete solution.
Endpoint DLP
Endpoint DLP focuses on protecting data directly on user devices such as laptops, desktops and servers. Instead of watching traffic at the network level, it monitors actions performed by users and applications on the device itself.
Endpoint DLP can see when a user copies data to a USB drive, uploads a file to a web app, prints a document or pastes content into a browser. Because it operates at the device level, it can enforce controls even when the user is off the corporate network.
This visibility makes endpoint DLP valuable for understanding how data is used in daily workflows. It allows organizations to apply controls closer to the point of action and respond in real time.
At the same time, endpoint DLP can be challenging to manage. Agents must be deployed and maintained across many devices. Policies can become complex and overly restrictive if they are not carefully tuned. Without strong classification and context, endpoint DLP can generate false positives that frustrate users and overwhelm security teams.
Endpoint DLP works best when organizations need direct control over user actions and when they can support agent deployment and policy management at scale.
Cloud-Based DLP
Cloud-based DLP emerged as organizations moved data into SaaS platforms and cloud infrastructure. Instead of focusing on networks or devices, this approach protects data where it lives and moves in cloud environments.
Cloud DLP solutions typically integrate with SaaS applications, cloud storage platforms and sometimes AI tools. They scan data at rest, monitor sharing and access controls and detect risky activity such as public exposure or excessive permissions.
One of the key advantages of cloud-based DLP is visibility. It helps teams understand where sensitive data exists across cloud services and how it is shared. This is especially important as collaboration tools and third-party integrations become more common.
Cloud DLP can also struggle if it relies solely on pattern matching or static rules. Without context, it may flag benign sharing as risky or miss subtle misuse. Coverage can vary depending on the depth of integration with each platform.
Cloud-based DLP is essential for organizations that rely heavily on SaaS and cloud infrastructure. It provides insight that network and endpoint tools cannot reach on their own.
How do different types of DLP work together?
No single type of DLP covers every risk. Network, endpoint and cloud-based solutions each see a different slice of data activity. Network DLP watches traffic leaving the environment. Endpoint DLP observes user actions at the source. Cloud DLP provides visibility into data stored and shared in cloud services.
Modern data environments require a more connected view. Data may originate on an endpoint, move through a SaaS app and eventually leave the organization through an integration or API. When DLP tools operate in isolation, gaps appear. Alerts lack context and teams struggle to understand what truly matters.
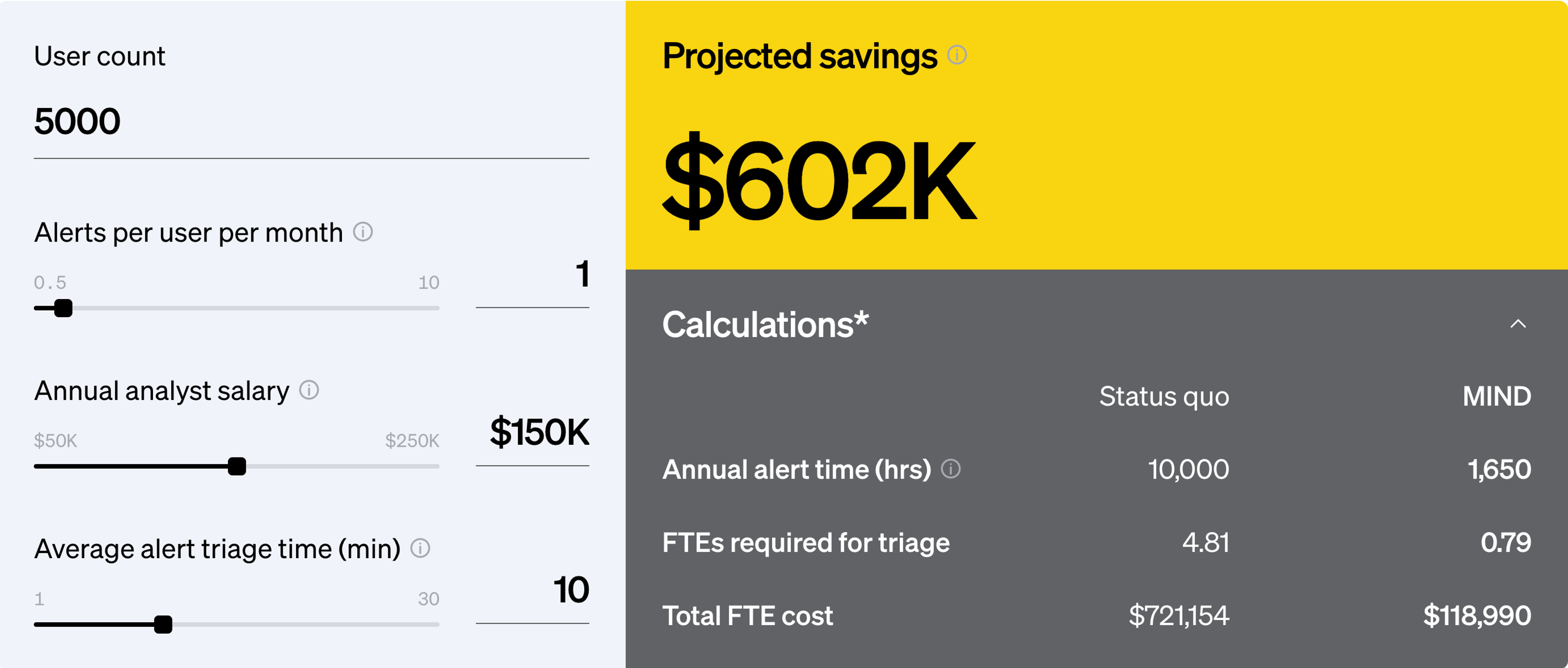
That’s why many organizations now look for ways to combine signals across these layers. When content, context and behavior are considered together, DLP becomes less about blocking and more about understanding risk.
How do I choose the right mix of DLP coverage?
Selecting DLP solutions is not about picking a single category. It’s about understanding where your data lives, how it moves and which risks matter most to your organization.
Network DLP can still play a role in controlling outbound traffic. Endpoint DLP helps protect data at the point of use. Cloud-based DLP brings visibility to SaaS and cloud environments. Together, they form a more complete picture.
The goal is not more alerts or stricter rules. It’s clarity. When teams understand how data is used across the organization, they can protect it in a way that supports people, workflows and the business itself.