In today’s cyber-threat landscape, it’s no longer enough to say you’re protecting sensitive data. For organizations handling controlled unclassified information (CUI), the challenge is real: you must find it, protect it and prove you’ve done so. That’s why, for many defense-industry contractors and service providers, the phrase “CUI compliance” is more than jargon, it’s mission-critical.
Why protecting CUI is harder than you think
Handling CUI isn’t simply a matter of putting a locked file cabinet around your most sensitive documents. Several factors make it uniquely difficult:
- Visibility is inherently difficult. CUI must be shared across finance, legal, underwriting, project management and other teams essential to contract delivery. As it spreads across network shares, cloud tools, vendor environments and even generative-AI inputs, visibility fragments quickly. Without a clear, continuously updated inventory of where CUI lives and who touches it, organizations operate with critical blind spots.
- Control is widely distributed. In government contracting, large groups legitimately need access to CUI to support complex projects. Restricting access to a few individuals isn’t realistic. Instead, we need precise, autonomous controls that govern how CUI moves across devices, identities, networks, clouds and partners, because the data moves and our protections must move with it.
- Proof is now mandatory. Under frameworks like CMMC 2.0, organizations must justify why each person needs access, not just rely on project association. The “need-to-know” principle must be enforced and documented. This requires complete auditability: who has access to every piece of CUI, why they have it and how those controls are maintained over time.
- The threat environment has evolved. Advanced persistent threats, supply-chain attacks, insider risks and real-time exfiltration raise the bar for what effective protection must look like today.
In short: you’re dealing with where the data is, who has access, how it’s used and whether you can show you’ve secured it. That complexity demands a modern, holistic approach rather than a checkbox.
Why NIST 800-171 Rev. 3 matters
CMMC 2.0 Level 2 maps to the 110 controls of NIST SP 800‑171 Rev. 2 framework. For organizations that are subject to it, the latest standard from the National Institute of Standards and Technology (NIST SP 800-171 Rev. 3) signals the future of CUI protection. While Rev. 2 remains the enforced baseline for now, Rev. 3 offers insight into the trajectory of expectation.
Here are some of the key takeaways:
- Rev. 3 aligns the security requirements more closely with the controls of NIST SP 800‑53 Rev. 5 and the moderate baseline of SP 800-53B.
- The number of security requirement families expands (with new families like Planning (PL), System & Services Acquisition (SA), Supply Chain Risk Management (SR)).
- The standard introduces “organization-defined parameters” (ODPs) so that controls can be tailored, but also demands that to be defined and measurable.
- It removes ambiguity: the older “basic vs derived” categorizations are gone and wording like “periodically” has been eliminated to drive specificity.
The implication for you: if you’re already pursuing CMMC Level 2 (i.e., full NIST 800-171 Rev. 2 compliance), you’re on the right path. But Rev. 3 gives you a view into how the standard will evolve and how your controls must evolve to stay ahead.
What achieving CMMC Level 2 really means
If your organization is working toward or has achieved CMMC 2.0 Level 2, you’ve committed to the full set of NIST 800-171 Rev. 2 controls: 110 security requirements across 14 families. That means not just writing policies, but operationalizing access control, auditing, incident response, configuration management, media protection and more.
Level 2 certification qualifies you to work with CUI, but it’s not a point of completion. Long-term success depends on your ability to continuously uphold that standard and anticipate future obligations.
How MIND helps you bridge the gap, from compliance to continuous assurance
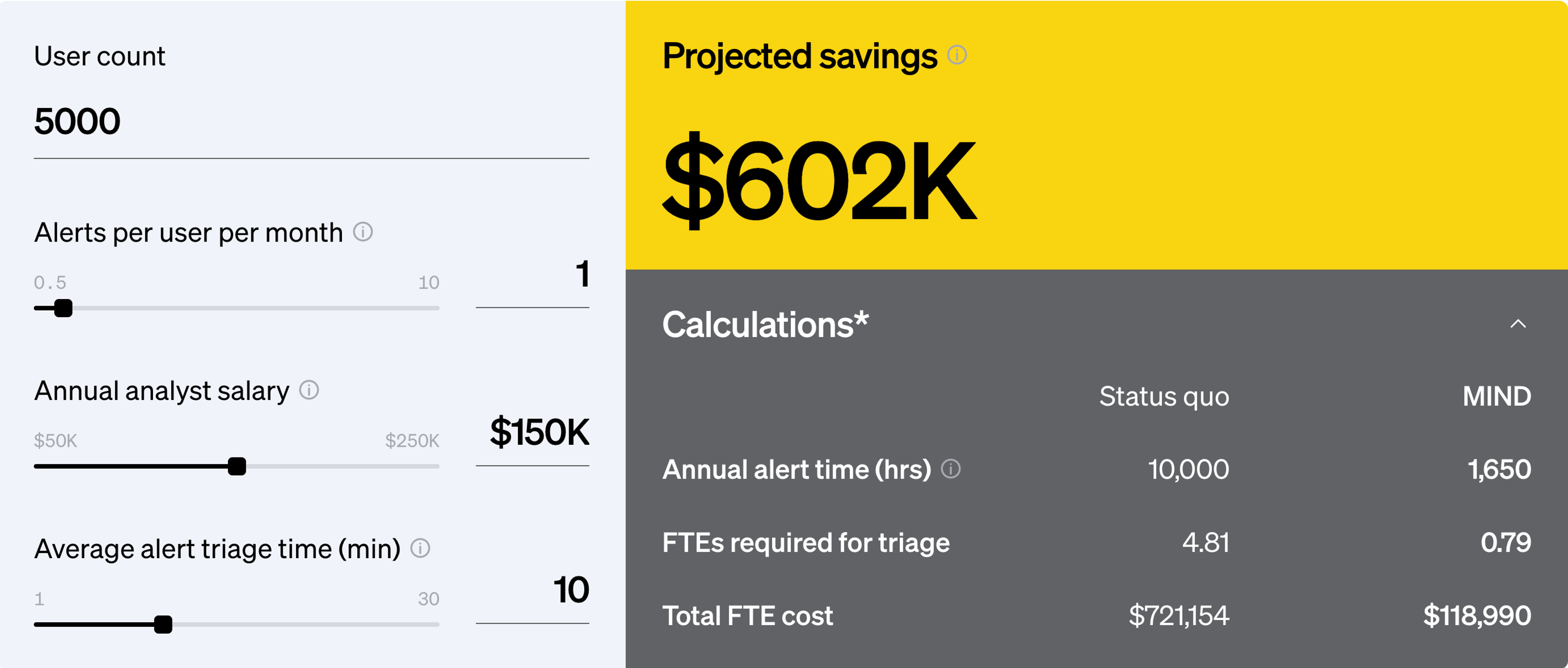
This is why organizations turn to autonomous DLP like MIND. We understand the practical challenges CISOs face, securing complex environments amid tight budgets, limited headcount and an evolving threat landscape. Our approach is to deliver Stress-Free DLP and help you mind what matters.
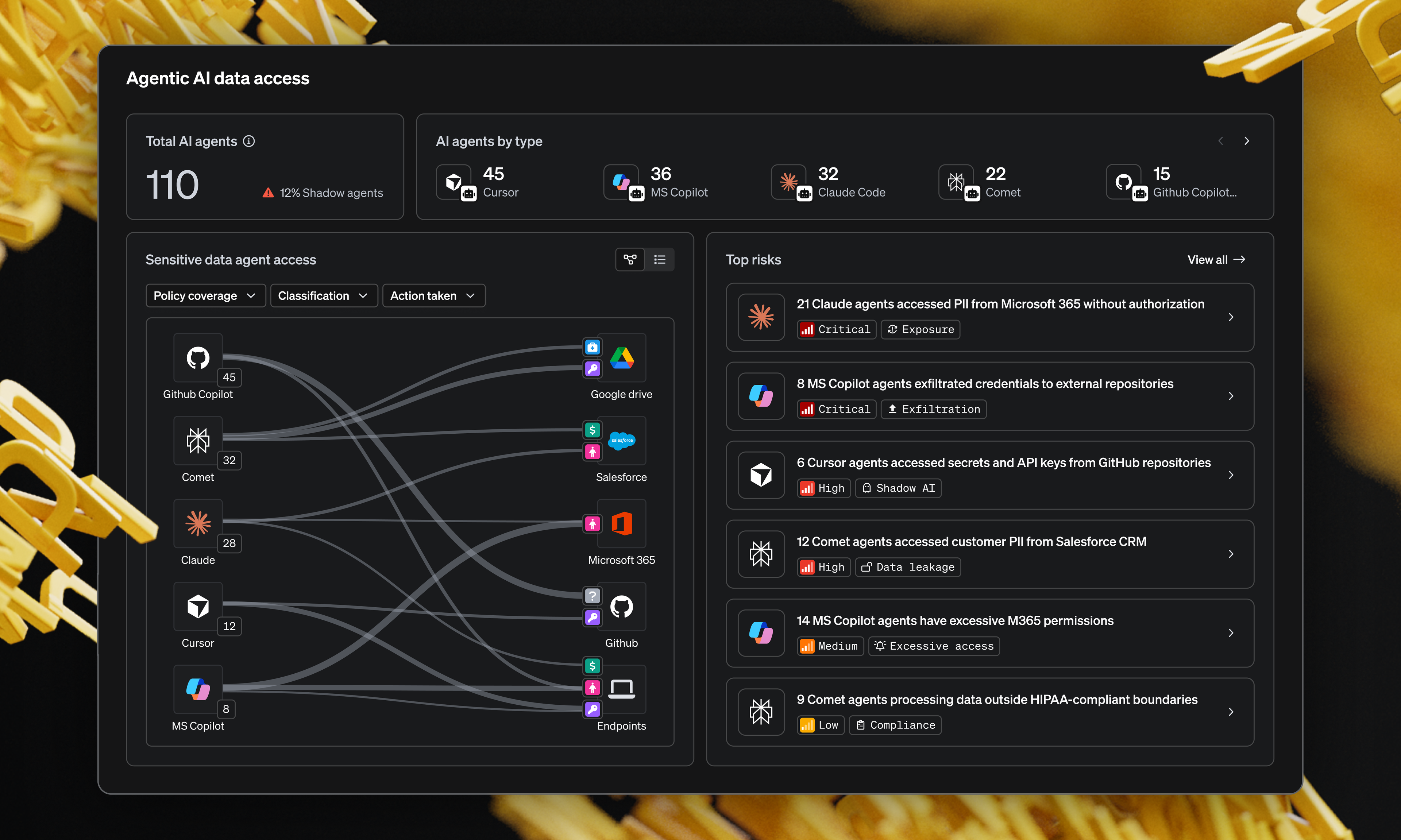
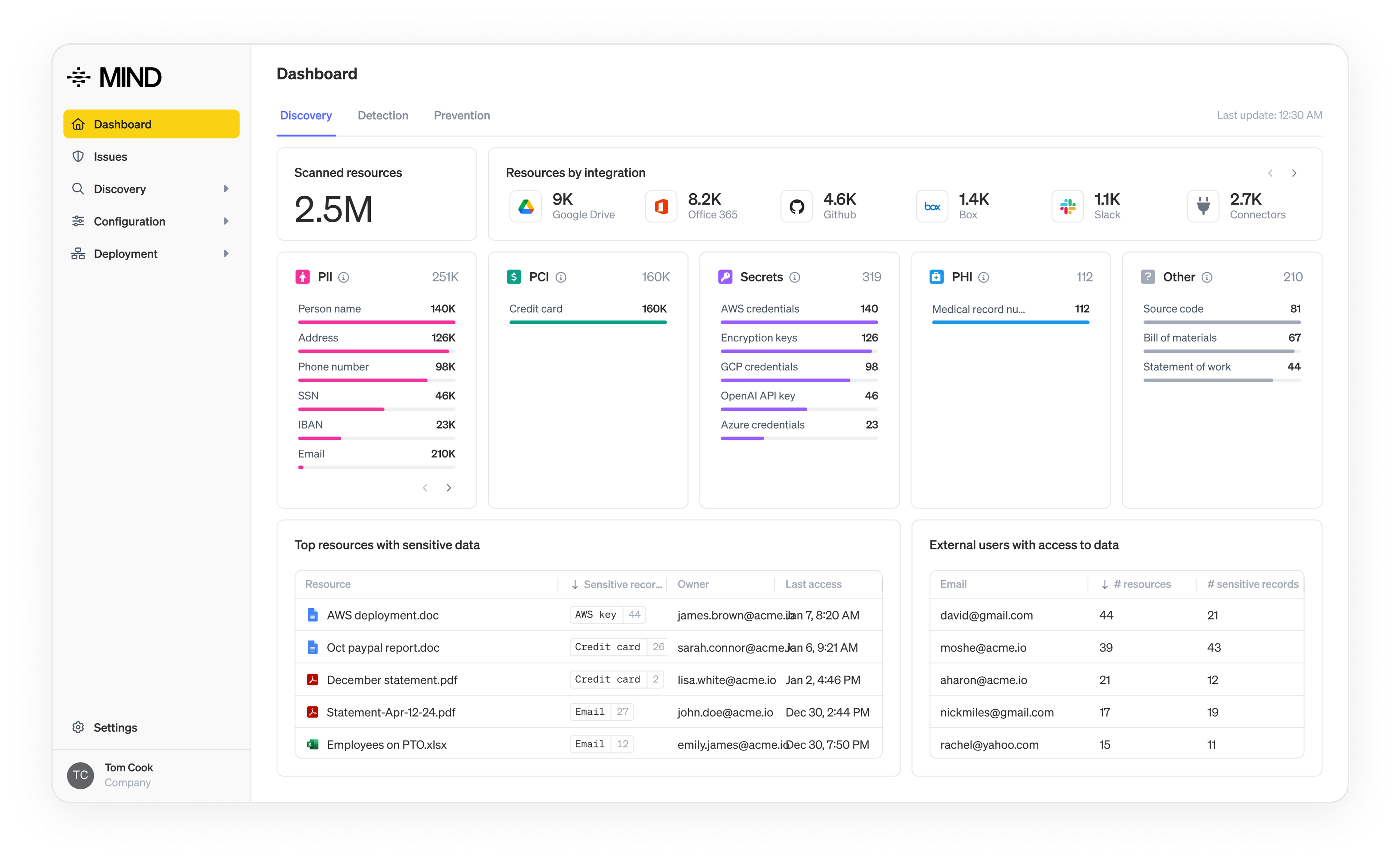
- Discover and classify CUI where it lives
We begin by discovering sensitive information across SaaS apps, on-premise file shares and endpoints. While most organizations have designated and highly controlled environments for CUI, the real risk lies in CUI elements stored outside of these areas. MIND can accurately classify CUI using our multi-layered classification engine and we alert if any CUI is found outside of the controlled storage areas. We classify it using context: who accessed it, where it came from and how it’s used. This ensures that the CUI you’ve contracted to protect is visible and, thus, protectable. - Enforce policy aligned to your controls
Once CUI is visible, MIND applies controls aligned with your NIST 800-171 requirements: controlling access, enforcing encryption, blocking risky activities, monitoring media transfers, restricting network egress and integrating with identity systems for least-privilege.
For example, you can define policies that block sensitive documents from syncing to unapproved collaboration tools or prompt users when a potential violation occurs, turning the policy into a real-time action. - Automate audit-ready evidence
Under CMMC Level 2, you must show auditors proof, not just that you wrote policies, but that they work. MIND’s dashboards capture access events, data movement, policy violations and remediation workflows. Your next assessment is no longer a scramble - it’s a status report. - Continuously validate and improve
Because threats evolve, so must your controls. MIND gives you continuous monitoring, analytics and risk scoring, identifying when a control drifts, when user behavior changes and when a vendor rises in risk. With these insights, you maintain a posture of assurance rather than just compliance. - Align to where the standard is heading
With NIST 800-171 Rev. 3 on the horizon, your investments today matter. MIND helps you build controls that are not just “enough for today’s audit” but scalable for tomorrow’s requirements, supply-chain risk management, planning controls, acquisition controls and measurable organization-defined parameters. You’re ready when the standard shifts.
Why this matters
Contractors in the defense supply chain are under increasing scrutiny. With major national security implications, the U.S. government expects non-federal systems processing CUI to meet robust standards. Failing to secure CUI isn’t just a regulatory issue; it puts your reputation, business and the mission at risk.
When you bring visibility, enforcement and proof together, you shift from a “compliance firewall” to a strategic data-protection posture. That’s what MIND helps you achieve.
Final thought
CUI is more than just secrets; protecting it helps ensure the integrity of the mission. Meeting NIST SP 800‑171 Rev. 3 (and by extension CMMC 2.0 Level 2 today) is more than a tick-box. It’s about transforming how you view, control and prove the protection of your most important data. With MIND, you can move from “we hope it’s protected” to “we know it’s protected.”
If you’re ready to move from reactive checklists to proactive assurance, and to ensure your CUI is truly under control, let’s talk. Because when you mind what matters, compliance becomes confidence.